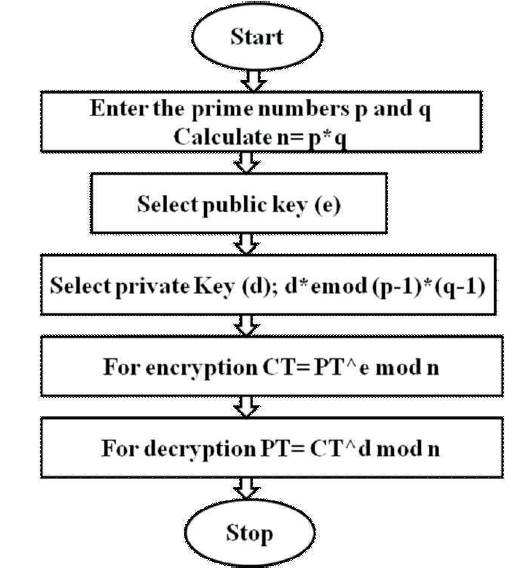
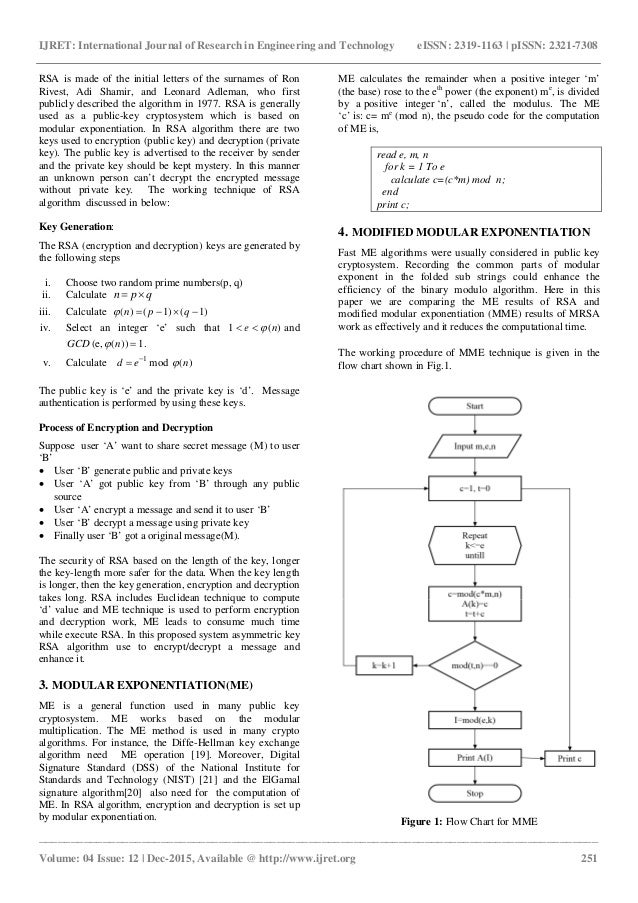
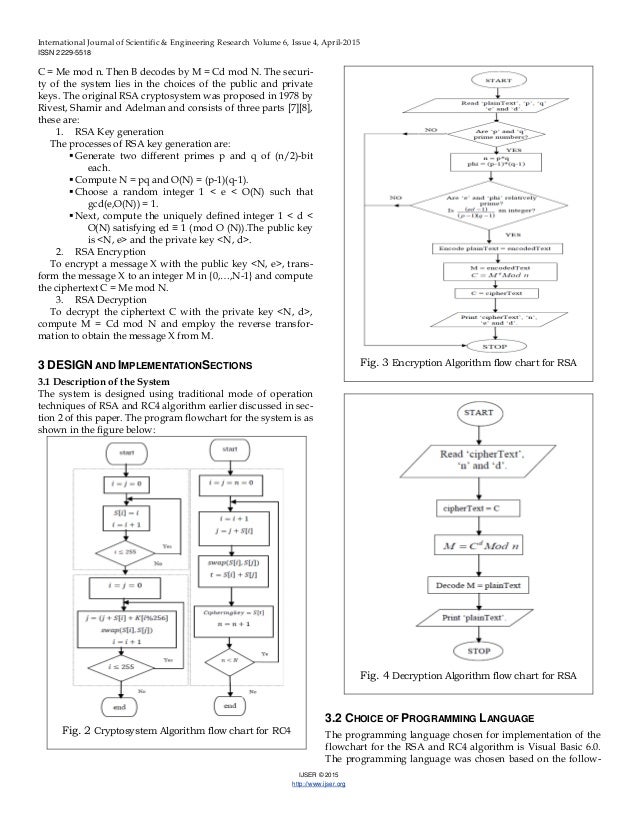
Flowchart For Rsa Algorithm

Generation of public and private key in rsa the flowcharts above shows how to generate a public and private key using rsa.
Flowchart for rsa algorithm. Here you will learn about rsa algorithm in c and c. Public key and private key. As the name describes that the public key is given to everyone and private key is kept private. Messages encrypted using the public key can only be decrypted with the private key.
Rsa is the last name beginning with the letter trio composed pieces together rsa is the most influ. Algorithms and flowcharts are two different tools used for creating new programs especially in computer programming. Rsa algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. Rsa can be used for both encryption and digital signature algorithms but also easy to understand and operate.
An algorithm is a step by step analysis of the process while a flowchart explains the steps of a program in a graphical way. Asymmetric actually means that it works on two different keys i e. The public key can be known to everyone it is used to encrypt messages. The keys for the rsa algorithm are generated the following way.
C language implementation of rsa algorithm. Displaystyle phi n p 1 q 1. Rsa has been extensively studied is the public key algorithm from the present. Rsa algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices.
Rsa public key encryption algorithm is 1977 by ronald rivest ron rivest adi shamir adi shamir and leonard adleman leonard adleman put together. The following is the procedure for generating a public and private key see flowchart. Rsa algorithm in 1978 by ron rivest adishamir and leonard adleman proposed a public key encryption algorithm. Encryption calculator for cryptography algorithms.
To create an rsa public and private key pair the following steps can be used. Although employed with numbers using hundreds of digits the mathematics behind rsa is relatively straightforward. Rsa algorithm is asymmetric cryptography algorithm.